IoT-based Space Security Solution
Suji Kim, Hwahyeon Park, Minseok Oh
Seoul Women’s University
Seoul, Korea
minohswu@swu.ac.kr
Abstract
We present a new concept of the space security to protect from potential risk. Using IoT-based space control unit and space security server, this concept provides reliable security level and low complex structure with simple certification process. It is thus suitable to use human-biometric information as certification password and easily construct intuitive alarming system associated with around IoT devices. In this paper, we discuss a concept system for practical applications with analysis of performance and complexity.
Keywords; IoT, Human-biometric, Space security
1. Introduction
After IoT(Internet of Things) was coined by Kevin Ashton [1] in 1999 and the term of IoT has been interpreted in extended way for many areas [2][3][4]. One of the best explanations for the IoT would be from ITU-T [5] as the following; “Global infrastructure for the society, enabling advanced services by interconnecting (physical and virtual) things based on existing and evolving interoperable information and communication technologies.
Although IoT technology is regarded as a fundamental infrastructure toward future Industry 4.0, security issue in IoT system is a challenge to be solved as soon as possible. For IoT security as well described in [6][7][8], we need to consider the security problem in cyber world as week as in real world because a boundary between online and off-line is getting closer.
One of security methods in real world is to block an intruder to enter a physical space. Door lock system can be a typical example for the space security in permitting a human who knows password. For real-time monitoring, we can use a surveillance system with supervisors. However, door lock requires a unique password at each door or the real-time monitoring system needs a supervisor who watches a screen all the time. Those methods do not seem desirable for large area application due to cost burden for massive door locks or operating surveillance system.
We present a new concept of space security based on IoT solution to improve security reliability, low complexity, and human-friendly interaction. In the concept, a unit space is used to judge whether a human or a device can stay on a given physical space or not. The size of the unit space is represented with 3D dimension (vertical X horizontal X height) and flexible depending on its capability.
As the number of space units to be used increases, the security level is linearly improved. Assume that ten security space units can be operating in a building. Although an intruder can pass a unit space, it would be difficult to pass all other units.
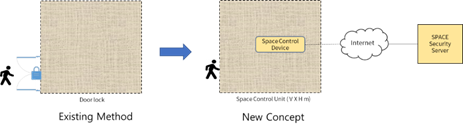
Figure1. New concept of space security
Each unit space has IoT device called Space Control Device (SCD), which collects bio-metric data of a target, and communicated with Space Security Server (SSS) for certification processing. When SCD detects a target who has approached a unit space and has collected some bio-metric information of the target, SCD sends it SSS (Space Security Server) with a query message. The SSS sends to SCD the result of the query as feedback via communication link after certification processing with high-performance computing. SCD is a simple and light device while SSS has high-end computing capability to analyze biometrics information collected from a unit space and manage database.
The new concept has scalable structure consisting of SCD, SSS, and IoT network so that it contributes to low cost system. For a large size of space security application, we just needs to increase the number of SCDs. A single SSS still can exist with reasonable computing capability, and a general communication link is used for IoT connectivity without additional cost burden.
IoT-based space security system provides human-friendly interaction in terms of password-asking-procedure and reaction procedure. SCD collects necessary biometric Information without human intervention from a unit space. If SSS sends a result of a target identification to SCD, SSS or SCD takes actions in human-friendly way using peripheral IoT devices, which they can control. For example, if a target is verified as an intruder, smart bulbs around the location turn on with red to inform current situation in rea-time.
We introduce our system in section 2, state system design with discussion of security reliability and complexity in section 3 and give a conclusion in Section 4.
2. IoT-based Space Security (ISS) System
In this section, we present the concept of IoT-based Space Security (ISS). When a human or device approach a unit space, Space Control Device (SCD) detects the moving, collect biometric-based information like face, bone structure, finger printing, and convey it to Space Security Server (SSS) via internet link between SCD and SSS.
IoT connectivity in ISS system plays a role to deliver data and control information in a local link of a unit space and in external via internet.
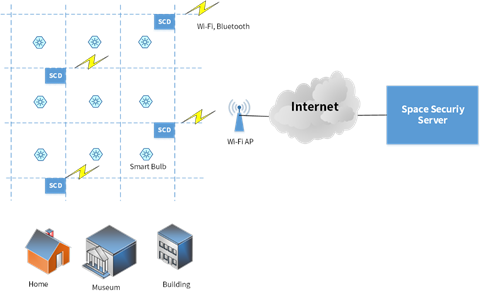
Figure 2. Overall Scenario of ISS
Figure 2 shows overall scenario in ISS system. Based on IoT defined in ITU-T [5], things and device are regarded as biometric information and SCD, respectively. The SCD can have sensors or camera to obtain bio-metric information camera such as face, bone structure.
The SCD in Figure 2 has two wireless communication links, Bluetooth [9][10] and Wi-Fi [11][12]. Bluetooth is used for control of smart bulb in unit space and Wi-Fi is link is used for internet connection between SCD and SSS to transfer bio-metric data and control message.
Each SCD is responsible for unit space identified as its unique location. The number of SCDs is decided according to size of overall space.
Space Security Server (SSS) is the server to have communication link with SCD and to analyze bio-metric information, manage database, and control all situations, which can occur.
In a practical system, since SCD cannot connect directly to internet, there is a gateway between SCD and SSS. In TCP/IP reference model for communication between SSS and SCD, HTTP and Wi-Fi can be understood as protocols for application layer and network interface layer, respectively. Figure 3. Shows overall communication link for ISS system

Figure 3. Communication Link in ISS
Use case for ISS is described as the followings:
1) A human approaches a unit space.
2) Space Control Device (SCD) in the unit space detects the moving through a sensor and then collects biometric information (picture, fingerprint, frame, etc.)
3) SCD sends the biometrics information data to Space Security Server (SSS)
4) SSS analyzes the biometric information and gives a positive or a negative feedback to SCD based on the result of the analysis.
5) After SCD received a feedback from SSS, it take an action to the human in positive or negative way depending on the result.
e.g.
a) In case of negative feedback, SCD regards the human as an intruder and then initiates alarming system
b) If the user is permitted, SCDs provides friendly guide beam
3. ISS (IoT-based Space Security) System Design
ISS System consists of four parts; Space Control Device (SCD), Space Security Server (SSS), Network and Connectivity, and Peripheral Devices.
3.1. Space Control Device (SCD)
SCD has detect a target moving a unit space, collect bio-metric information from the target, followed by transferring the data to Space Security Server(SSS). Figure 5 illustrates the structure of SCD composed by three modules, which are space detector, Biometric collector, and communication model.
Space Detector recognizes approaching of someone through sensors using ultra-sonic, infrared wave, sound, etc. If someone have been detected in the unit space, Bio-metric Collector gets some bio-metric information such as face picture, moving pattern, etc. Then SCD sends the data to SSS for analyzing access right of someone. The Communicator of SCD is responsible for communication link management in network interface and application layer, respectively. In Figure 4, Communicator is connected to Peripheral Devices to express a reaction scenario according to the result of SSS's feedback on the access right of someone.
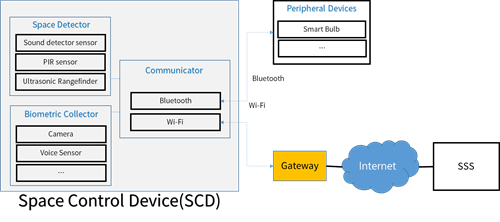
Figure 4. SCD Structure
Figure 6 illustrates an example of SCD operation, using detection sensors of sound and infrared, and camera for face picture.
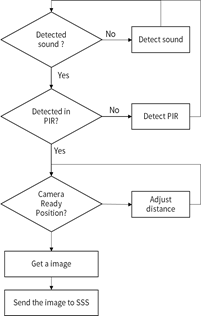
Figure 5. SCD Operation
3.2. Space Security Server (SSS)
Main roles of SSS is the server to analyze bio-metric information, and mange data base, control overall system. A single SSS exists in overall ISS system and communicates with SCD in application layer. Figure 6 shows six parts composed of SS; Database Manager, Bio-metric Analyzer, Device Manager, System Controller, and Communicator.
Database Manager is responsible for map management between each unit space and permitted group people. Each unit space has its unique location information and people group list with access right of the place.
Bio-metric Analyzer plays a role to analyze the bio-metric information to proceed certification process. Typically, this process requires high-performance computing capability. We can consider clouding computing [12] for cost-effective method
Communicator in SSS has a role to communicate with SCD in application layer. Figure 6 shows an example using HTTP protocol.
Device Manager is for control of peripheral device from SSS, while System Controller deals with overall system control.
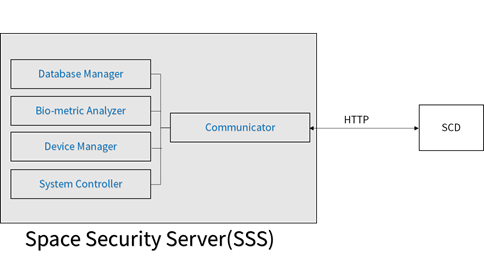
Figure 6. SSS Structure
Figure 7 illustrates an example of SSS operation for face recognition. SSS extracts a face image from the data sent from SCD and compares with the stored images of permitted group. By the result of the comparison, SSS sends SCD the feedback of 'permitted', or the feedback of 'not-permitted'.
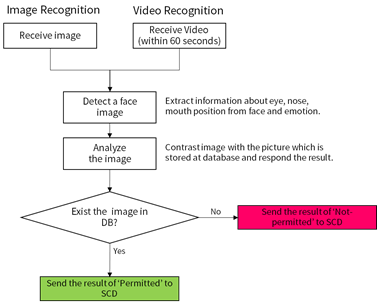
Figure 7. Face Recognition in SSS
3.3. Network and Connectivity
Network and Connectivity in ISS can be classified into local area link and wide area link. Local area networking is carried out within a unit space. In ISS system, we use Bluetooth and Wi-Fi connectivity for the local interface to control and manage devices and sensors around the unit space coordinated by a SCD.
Smart bulb is operated by SCD via Bluetooth link and distance between SCD and smart blubs should’ve at most 10 meters. For longer wireless link, Wi-Fi is used and provides service coverage up to around 50 meters in indoor. In addition, Wi-Fi is only a communication link to connected SCD to external network via a gateway [14]. Once Wi-Fi connection is established, SCD can communicate with SSS in external network using HTTP protocol in application layer.
3.4. Peripheral Devices
SSS or SCD can represent in intuitive way the result of a target certification in a unit space through the peripheral devices, which they can control. With smart bulbs as peripheral devices, if SSS judges a human as not-permitted person, SCD or SSS can makes alarming beam by turning on smart bulb with red color so that the space is recognized as an intruded zone.
3.5. System Evaluation
Performance of ISS System
is measured in terms of security reliability and implementation complexity. Assume
that the number of unit space in ISS is n, ![]() is overall security
reliability,
is overall security
reliability, ![]() is security
reliability of
is security
reliability of ![]() . Accordingly,
although the security reliability of SCD is relatively low due to low-end
device capability, overall security reliability can be achieved by combing
multiple SCDs as the following equation is shown.
. Accordingly,
although the security reliability of SCD is relatively low due to low-end
device capability, overall security reliability can be achieved by combing
multiple SCDs as the following equation is shown.
![]()
In addition, since IoT connectivity provides flexibility in combining multiple bio-metric certifications, the reliability in SCD can be improved with more than one bio-metric information.
In the aspects of implementation complexity, as the number of SCDs easily increase and SSS can be constructed using cloud solution. There is no serious working cost to extend service area compared with the existing method.
4. Conclusion
The term of security is generally used to protect from potential harms or to minimize any risks in many areas including computing and building management. When we look back current mega trends of IoT-based convergence in every area, we needs wide range of security concept and solution since we can expose potential harms on more connection of things over on-line and off-line situation. It is thus useful to understand space security management in a fundamental way.
We have proposed a new concept of IoT-based space security. In the comparison with the traditional methods such as door lock, real-time surveillance system, the space security scheme is to provide easy deployment and higher security level according to adding the number of unit space for protection. In addition, this scheme allows creative reaction by using other IoT devices according to the result of real-time detection of a given space. Space security system can trigger step-by-step alarming system to an intruder who has entered a space. On the other hand, a permitted person in a location enriches context-aware guides such as mood-lights, and automatic control of around devices, which the space security system can provide.
The most interesting benefit of the scheme is scalable structure attached to a physical location in terms of unit space dimension. Since the unit space basic management requires a simple IoT device to manage the unit space, it naturally gives low cost construction customized to a requirement of a target in terms of security level, size of overall space, and alarm representation. The over security level is getting higher as the number of unit space is added, which means that overall security can guaranteed in spite of relatively low of security level in a unit space. In addition, we can choose specific bio-metrics among iris, face, pam print, voice, walking pattern, etc, and measure overall security level by combining the results from unit spaces
Several areas remains for further works. One of interesting topics will be to explore more insights on deciding values in terms dimension of a unit space, and the number of unit spaces in overall service area. Space security concept is not limited to a human target. If we assume a things or object (device) being placed in a space, we can find new applications in more creative way.
References
[1] Ashton, K, “Internet of Things” Thing. RFID Journal, 22, 97-114, 2009
[2] Matthew Gigli, Simon Koo, “Internet of Things, Services and Applications Categorization”, Advances in Internet of Things, pp. 27-31, 2011.
[3] Somayya Madakam,R. Ramaswamy,Siddharth Tripathi, “ Internet of Things (IoT): A Literature Review”, Journal of Computer and Communications , vol.03 No.05, pp. 164-173, May. 2015
[4] GSMA, “ From Concept to Delivery: The M2M Market Today. GSMA Intelligence”, Feb. 2014.
[5] Telecommunication Standardization sector of ITU, “Overview of the Internet of things,” Recommendation ITU-T Y.2060, June 2016.
[6] Engin Leloglu, “Review of Security Concerns in Internet of Things”, Journal of Computer and Communications, Vol. 5. No.1, pp. 121-136, Jan. 2017
[7] Joshua J. Pauli , “Refining Use/Misuse/Mitigation Use Cases for Security Requirements”, Journal of Software Engineering and Applications, pp, 626-638, 2014
[8] Lobna Yehia, Ayman Khedr, Ashraf Darwish, “Hybrid Security Techniques for Internet of Things Healthcare Applications”, Advances in Internet of Things vol.05 No.03, pp.21-25, Jul. 2015
[9] Bluetooth SIG, “Specification of the Bluetooth System v1.0 B December 1st”, Dec. 1999
[10] Thomas Djotio Ndie, Claude Tangha, Tam Sangbong, Armstrong Formenah Kufor, “Mobile Applications Provisioning Using Bluetooth Wireless Technology”, Journal of Software Engineering and Applications vol.4 No.2, pp. 95-105, Feb. 2011
[11] Oran Sharon, Yaron Alpert, “Single User MAC Level Throughput Comparison: IEEE 802.11ax vs. IEEE 802.11ac”, Wireless Sensor Network vol.9 No.5, pp. 166-177, May 2017
[12] Yiru Wu, Yinghong Ma, Hongyan Li, Jiandong Li, “ Performance Evaluation of Flows with Diverse Traffic and Transmission Rates in IEEE 802.11 WLAN”, Communications and Network, vol.5 No.3B, pp. 634-640 Oct. 2013
[13] Michael Perez, Sanjeev Kumar, “A Quick Survey on Cloud Computing and Associated Security, Mobility and IoT Issues”, Journal of Computer and Communications, vol.5 No.12, pp. 80-95, Oct. 2017
[14] Yepeng Ni, Fang Miao, Jianbo Liu, Jianping Chai , “Implementation of Wireless Gateway for Smart Home”, Communications and Network, vol.5 No.1B, pp.16-20 , Nov. 2013